The Google authenticator app adds an easy to use true two factor login (rather than just an extra password, I’m looking at you online banking). It is time limited and each code is valid one for 30 seconds, however this can be changed.
There are other guides out there which describe the setup but these follow the assumption that you will be using passwords to login rather than public keys.
This method is tested for Ubuntu 14.04.1 but will likely work for any distro that has a recent release of openssh (v6.6+). The following commands assume you are logged in as root, if not prefix with sudo.
First step is to install the authenticator.
aptitude install libpam-google-authenticator
Next, setup the authenticator for your login or root.
$ /usr/bin/google-authenticator
Do you want authentication tokens to be time-based (y/n) y
https://www.google.com/chart?chs=200x200&chld=M|0&cht=qr&chl=otpauth://totp/...
[QR CODE]
Your new secret key is: D3WF27FKWZA5TAO3 (not real :P)
Your verification code is 123456
Your emergency scratch codes are:
12345678
12345678
12345678
12345678
12345678
Do you want me to update your "/home/sam/.google_authenticator" file (y/n) y
Do you want to disallow multiple uses of the same authentication
token? This restricts you to one login about every 30s, but it increases
your chances to notice or even prevent man-in-the-middle attacks (y/n) y
By default, tokens are good for 30 seconds and in order to compensate for
possible time-skew between the client and the server, we allow an extra
token before and after the current time. If you experience problems with poor
time synchronization, you can increase the window from its default
size of 1:30min to about 4min. Do you want to do so (y/n) n
If the computer that you are logging into isnt hardened against brute-force
login attempts, you can enable rate-limiting for the authentication module.
By default, this limits attackers to no more than 3 login attempts every 30s.
Do you want to enable rate-limiting (y/n) y
You’ll need to either scan the provided QR code via the authenticator app or follow the provided url.
Now you are enrolled in two-step authentication, congrats.
Next is to update PAM to accept Google Authenticator tokens. Update /etc/pam.d/sshd to include the follow at the top of the file (above @include common-auth).
#Google Authenticator
auth sufficient pam_google_authenticator.so
Sufficient is used rather than required here because required would prompt for the password after the code is entered which is not what we want as public keys are being used.
The final step is to setup the ssh server to accept public keys and allow keyboard interaction. Open /etc/ssh/sshd_config and make the following changes. But take a backup first.
# Add this if not present
PubkeyAuthentication yes
# This allows sshd to ask for the verification code
# after the public key is accepted
AuthenticationMethods publickey,keyboard-interactive
# Change the following to yes, it is no by default
ChallengeResponseAuthentication yes
# Also disable password logins
PasswordAuthentication no
# This should be present, but add if not present
UsePAM yes
Now restart the ssh server.
service ssh restart
Important: Don’t close your current session until you know the login is working correctly, as you may get locked out.
Time to test, open a new ssh connection to your box, you should now be greeted like this:
Using username "root".
Authenticating with public key "my-public-key" from agent
Further authentication required
Using keyboard-interactive authentication.
Verification code:
If this fails, you can restore the backup you made of the sshd config (you did make one?), remove the authenticator from the pam config. and restart ssh.
Google Authenticator Project: https://code.google.com/p/google-authenticator/
Authenticator App: Play Store | Apple App Store | Windows Phone
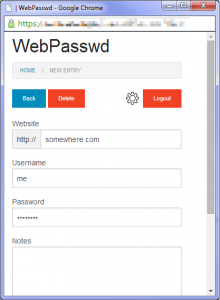 WebPasswd is a password app that I have been working on, its a self hosted PHP app, that stores usernames and password (along with notes) in an encrypted file.
WebPasswd is a password app that I have been working on, its a self hosted PHP app, that stores usernames and password (along with notes) in an encrypted file.